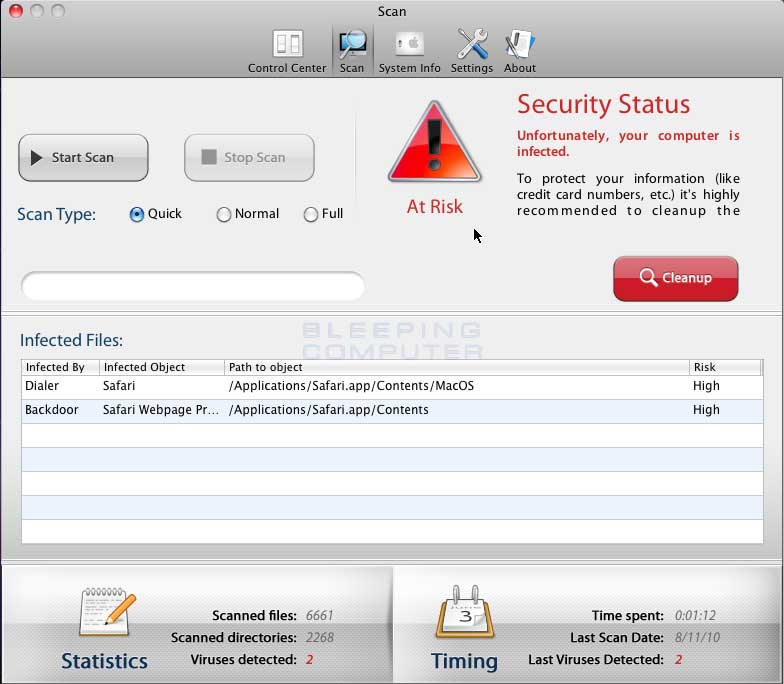
Laser Defenders are, name-wise, anti-tank infantry that use a laser under the codename 'Defender'. They are covered with ceramic armor to resist against the heat generated by their weapons. Laser Defenders are, name-wise, anti-tank infantry that use a laser under the codename 'Defender'. They are covered with ceramic armor to resist against the heat generated by their weapons.
- Laser Defender (flyn Nick) Mac Os Catalina
- Laser Defender (flyn Nick) Mac Os Download
- Laser Defender (flyn Nick) Mac Os X
EDDB welcomes all new players to Elite: Dangerous! 22-11-20
The Epic Store giveaway draws many new players to the game and I welcome all of you to take part in this epic space adventure! To make it easier understand EDDB here are some FAQs for starters:
What is EDDB?
EDDB is a website which tries to act as a database of all the data available in the game. In general EDDB tries to help finding stuff which players are looking for.
Where does the data on EDDB come from?

The data which can be found on EDDB is 100% community generated. There is no regular data dump from Frontier. Systems, stations, commodity prices, outfitting or shipyard information - all this information is 100% coming from the actual player base.
How can you help keeping the data on EDDB up to date?
Short answer: Use a program like EDMC while playing the game, and every time you visit a system or a station, EDDB is being updated with the latest data.
Long answer: Not only EDDB but most of the Elite community websites are connected to a realtime data network called EDDN. The basic idea is that players use an EDDN client while playing the game and for instance if the player docks on a station, the latest station information is being transmitted to the EDDN network. Every website which supports EDDN gets those updates immediately. There are many client programs, offering different kinds of functionality. However, one simple to use client is EDMC, so I recommend this one for starters.
Windows 10 has crossed the halfway mark — more than 50 percent of desktops now run Microsoft’s newest operating system. The shift forms part of a larger pattern: As noted by recent survey data, more than three-quarters of companies cited “at least one innovative operational technology that they have adopted or are considering” in 2019.
The challenge? Increasing security risk. As network attack surfaces expand and operating systems are tasked to manage on-premises, cloud-based and even mobile deployments, the realities of risk come home to roost. Data confirms this concern, as 79 percent of companies rank cyber-risk as a top five concern even as their confidence to assess, detect and mitigate cyberattacks falls year over year.
To help strengthen and streamline security, Windows 10 includes new features that drive new operational best practices. Here’s what businesses need to know.
Windows 7 Security vs. Windows 10 Security: What’s the Difference?
Nick Cavalancia, Microsoft MVP and founder of Techvangelism, puts it simply: “Windows 10 security features are laser-focused on protecting and preventing current, specific forms of cyberattack.”
While popular predecessor Windows 7 prioritized “securing the endpoint,” Cavalancia notes that the focus was more general: “Keep the bad stuff from running.” Application, network and data protection simply weren’t part of the equation.
Windows 10 also takes a different approach to updates. By default, the OS automatically — and randomly, at least once every 17 to 22 hours — checks for new updates. Along with typical “patch Tuesday” updates that happen once per month, smaller security updates are deployed on an as-needed basis. Although absolute protection isn’t possible, this type of on-demand framework helps keep the largest number of devices current on updates and reduces overall risk.
Windows 10 Security Features: S Mode, Defender Security Center and More
What specific features are new in Windows 10 that support Microsoft’s general approach to security? It’s not a small list, but as Cavalancia points out, businesses will likely appreciate those features that help secure network environments against employees who are more focused on the task at hand than on defending network data. Some of the top features that “protect the user from themselves” include:
- Windows Defender Smart Screen — This protects users by blocking access to known, nonsecure sites.
- Windows Defender Application Guard — This makes it possible to access untrusted sites “but does so in an isolated virtual container, blocking access to system resources.”
- Windows 10 S Mode — Shadow IT remains alive and well — 76 percent of employees have accessed resources on work devices without IT permission. S mode helps control shadow IT sprawl by limiting app installation to those from the Microsoft Store.
- Windows Sandbox — If organizations choose to allow broader application permissions, Windows Sandbox ensures new apps run in isolated virtual containers to prevent full system access.
- Remote Desktop Biometrics — As noted by Cavalancia, “Remote desktop protocol (RDP) attacks are still one of the main ways ransomware attacks are initially carried out.” Windows Hello for Business leverages biometric authentication to reduce the risk of RDP compromise.
Laser Defender (flyn Nick) Mac Os Catalina
How to Manage Top Security Threats in Windows 10
For companies just making the move to Windows 10, it’s worth tackling the basics before moving on to more strategy-driven protection. Start with:
- Handling user accounts and identity — Deploying a combination of tools such as Microsoft Passport, Windows Hello and Microsoft Azure Active Directory helps limit potential use risk. Passport provides a multifactor password alternative, while Hello deploys biometrics and Active Directory takes identity and access management (IAM) into the cloud. Cavalancia makes it clear that “bad guys can’t do anything without credentials.” Leveraging Windows 10 tools to implement least-privilege protocols confounds most cybercriminal attacks.
- Securing physical devices — Here, it’s a good idea to implement UEFI Secure Boot and create a Windows 10 save point. Secure Boot helps maintain OS integrity by preventing hardware-based malware installations, while save points provide a safety net if new application installations go south.
- Protecting critical data — Microsoft BitLocker empowers configurable disk encryption, while Enterprise Data Protection tools permit integrated data separation and containerization along with file-level encryption to defend data at scale.
- Detecting new threats — Microsoft Defender tools, including Device Guard, allow businesses to lock down desktops and devices and compel applications to prove their trustworthiness, while the Windows Defender Security Center makes it easier for IT teams to control firewall, anti-virus and anti-malware solutions.
Windows 10 Implementation Guide: Cybersecurity Best Practices
Approach is everything. Even with the best tools available, businesses need to implement security best practices that align with both organizational goals and existing technology deployments.
First, define your update schedule. For business IT departments, there’s a tendency to avoid immediate updates in case the latest Windows version causes problems for current deployments — but waiting too long puts critical data at risk. Best bet? Find a middle ground. As noted by ZDNet, the Windows Update for Business lets IT teams defer quality updates for 30 days and feature updates for two years. Settle on a schedule that works for you — between seven and 15 days is often enough time to ensure there are no compatibility issues — and then stick to it.
It’s also a good idea to “look for ways to enhance existing security with Windows 10 integrated solutions.” While third-party tools can help address specific concerns, limiting the number of interlocking technologies on your network also limits the number of potential gaps.
Laser Defender (flyn Nick) Mac Os Download
Finally, Cavalancia recommends that businesses “always, always, always think about security as a layered defense.” No single solution provides complete protection. By regularly assessing their security posture, companies can find critical weaknesses and identify the best solution — Windows or otherwise — to increase overall protection.